

The Digital Credential Scenario Innovation Challenge is an innovation contest focused on applications of the Digital Identity Wallet. It encourages participants to leverage technologies such as Verifiable Credentials (VCs) and Decentralized Identifiers (DIDs) to propose digital service concepts that are both practical and socially valuable.
Competing teams may design solutions in domains such as campuses, public services, and transportation, creating innovative scenarios that enhance privacy protection and strengthen user autonomy. The challenge aims to promote convenient public services, improved government efficiency, and digital solutions to pressing social issues.
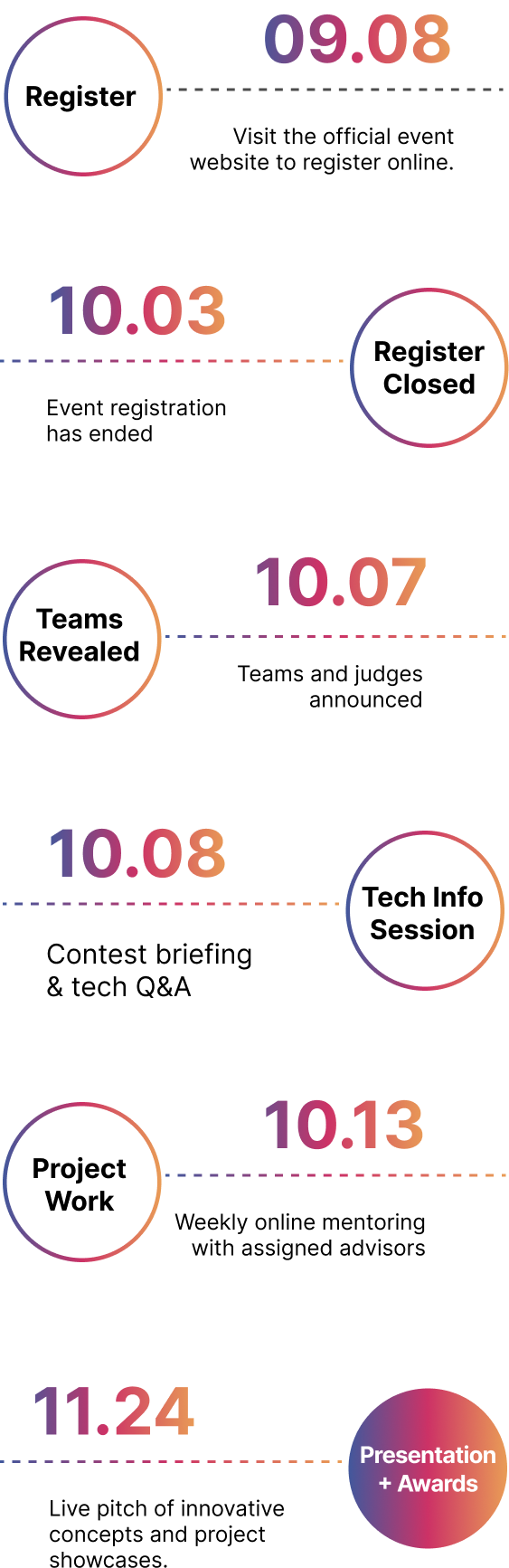
Successful integration with Taiwan Digital Identity Wallet (TW DIW) or demonstration of the credential issuance, presentation, and verification process.
Implementation of a complete service workflow within the application scenario (e.g., borrowing books, check-in, verification).
System robustness and completeness to ensure the solution can be realistically deployed and operate stably.
Demonstrates innovative use of technology.
Application scenario shows breakthrough or forward-thinking concepts.
User interface or interaction design introduces novel and engaging experiences.
User roles and data flows are clearly defined and feasible.
Core processes of “Authorization → Usage → Verification → Record” are effectively demonstrated.
Provides a clear description of service flow, interaction roles, and user context.
Interaction design is intuitive, seamless, and context-appropriate.
Includes user guidance, error handling, and feedback mechanisms.
Considers diverse user contexts (e.g., elderly users, mobile devices, offline scenarios).
Showcases unique ideas and creative perspectives with strong originality.
Presentation is clear, impactful, and effectively communicates the design core.
Q&A demonstrates technical understanding and scenario-oriented thinking.
Reflects the team’s collaboration, integration, and adaptability during the final pitch.
This competition focuses on the application of the Digital Identity Wallet, encouraging participants to use Verifiable Credentials (VCs) and Decentralized Identifiers (DIDs) to design innovative scenarios that promote convenient public services, government efficiency, and digital solutions for social issues. More information: https://civictech.moda.gov.tw/about/
A Digital Identity Wallet is a secure digital tool for managing and presenting various credentials (e.g., student IDs, driver’s licenses, training certificates). It is based on international standards such as VC and DID, supporting features like offline verification, selective disclosure, and biometric authentication to enhance privacy and user autonomy.
It is not an e-wallet or a single-purpose identity tool, but rather a platform for securely managing diverse digital credentials. More information: https://wallet.gov.tw/zh-tw
The competition is open to all students and the general public nationwide. Cross-disciplinary collaboration is encouraged. Teams may consist of 1–5 members. Participants under 18 must submit a legal guardian’s consent form. Go register: https://forms.gle/mKWCV1m2LhA5hjc39
Participants must select a group category at registration:
If all members are current students → register for the Student Group.
If the team includes non-students → register for the Open Group.
Mixed teams are not eligible to register under the Student Group.
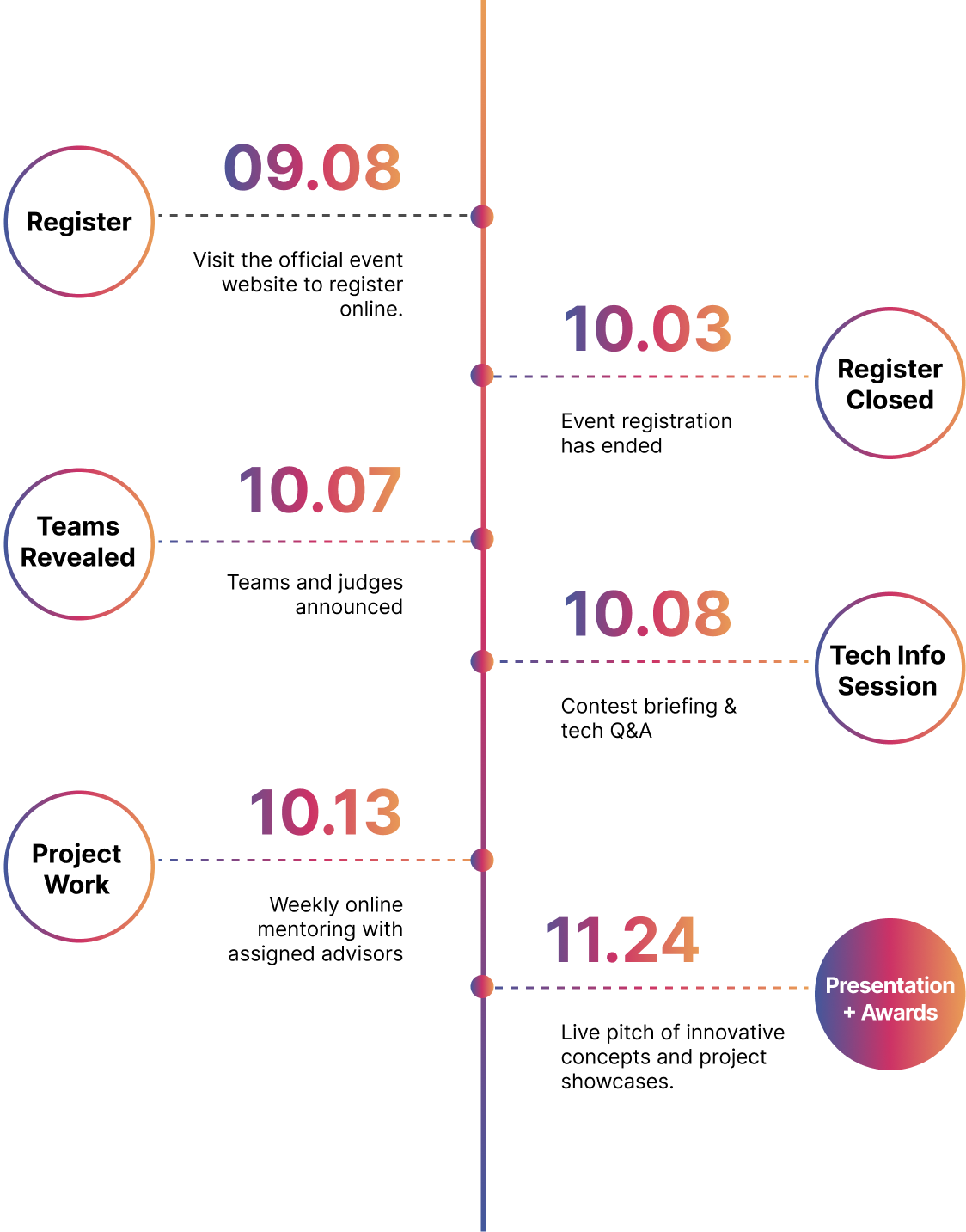
📌 Registration: September 8 (Mon) – October 3 (Fri), 2025
📢 Announcement of Teams & Mentors: October 7 (Tue) (published on the official website)
💻 Technical Briefing: October 8 (Wed)
🛠️ Implementation Period: October 13 (Mon) – November 11 (Tue) (including technical mentoring)
🏆 Final Presentation & On-site Evaluation: November 12 (Wed)
🎉 Award Ceremony & Closing: November 12 (Wed), 16:10–17:00
Entries must address the theme “Digital Credentials × Scenario Applications × Social Innovation” and incorporate the following technical elements:
Verifiable Credentials (VCs): Cryptographically signed, verifiable offline, reducing data leakage risks.
Decentralized Identifiers (DIDs): Privacy-preserving, independent of centralized identity linkage.
Decentralized Storage: Credentials stored on personal devices; trust lists recorded on public blockchains.
Local Biometric Authentication: Fingerprint/face data stored locally, never transmitted to the cloud.
Selective Disclosure & Zero-Knowledge Proofs: Users disclose only necessary data, enhancing privacy.
Participants are expected to use the Taiwan Digital Identity Wallet (TW DIW) as a core technological framework to design innovative services with real-world implementation potential. Solutions should demonstrate practical applications across domains such as education, public services, and mobility and daily life, showcasing how verifiable credentials can enhance trust, privacy, and user autonomy in everyday scenarios.
Yes. The competition offers a Technical Briefing and Mentorship during the implementation period. Expert advisors will guide participants through technical challenges, and assigned mentors will provide ongoing technical support and practical coaching.
More details: https://civictech.moda.gov.tw/expert-mentorship/
Yes. To promote openness and community sharing, all winning projects must be published on the Public Code Platform(https://code.gov.tw) within 10 days after the finals. Projects must pass security review and comply with open-source licensing requirements.
Failure to comply may result in delayed or revoked funding disbursement.
Prizes will be awarded to the designated team representative and must be reported in accordance with applicable tax laws.
Awards exceeding NT$20,000 are subject to 10% withholding tax.
For foreign participants, 20% withholding tax applies.
Each participant may only join one team and cannot register for multiple teams.
Registration information must be complete. Missing information must be supplemented within 2 days upon notice.
All submissions must be original works and comply with copyright and open-source licensing requirements. Non-compliance may result in disqualification.
All winning projects must undergo source code security scanning to ensure compliance with the competition’s security requirements, and the scan report must show no medium- or high-risk vulnerabilities. Winners may choose to conduct the scan themselves or authorize the organizer to perform the scan.
For self-conducted scans, participants must use common vulnerability scanning tools (e.g., open-source code analysis tools or dependency vulnerability scanners) and submit a complete report. The report must include the tool name and version, scan date, scan scope (e.g., code modules or files), list of detected vulnerabilities (including vulnerability type, severity level, impact scope, and remediation recommendations), as well as remediation status (if applicable).
If the scan is performed by the organizer, the winners must submit the full source code. The organizer will conduct the scan and provide the report. All vulnerabilities must be remediated by the winning team, and a re-scan must be performed with a final report submitted to confirm that no medium- or high-risk vulnerabilities remain. The organizer reserves the right to review the reports, and if a report fails the review or reveals medium- or high-risk vulnerabilities, the organizer will notify the winning team and require remediation and resubmission of the report within a specified timeframe.